A trojan horse or Trojan virus is malware in the shape of legitimate software. However, it looks legitimate but can get access to your system. It is remarkably designed to steal, disrupt, damage the data stored in the system. Also, it brings some other harmful action on the data or network.
It is considered a bona fide software or application to trick you in some kind of social engineering that makes the Trojan function by making it executed and loaded. Through this software, the cyber-criminals become enable to spy on us, steal our personal secret data, and get background access to the system. Once installed, it can execute the function it was designed for.
A Key Concept of Trojan virus?
If you are a literature student then you would probably know about that the term “Trojan”. It derives from the ancient Greek story. It is about the hollow wooden Trojan horse which causes the fall of Troy. The Greeks hid inside of the horse and Trojans welcomes the horse as a gift. Then, the Greeks attack the city at night and thus lead to its fall. A Trojan virus is yet another horse that secretively filled other viruses that can provide damages to your system.
It is often regarded as the Trojan horse virus or Trojan virus but these names are quite incorrect. Because trojan does not self replicate, unlike other viruses. It pretends to be a useful application of content while hiding malicious sources. It will be more beneficial to consider Trojan as just another term that hackers use for malicious activity and malware delivery hackers use.
Trojans Virus: How does it Work?
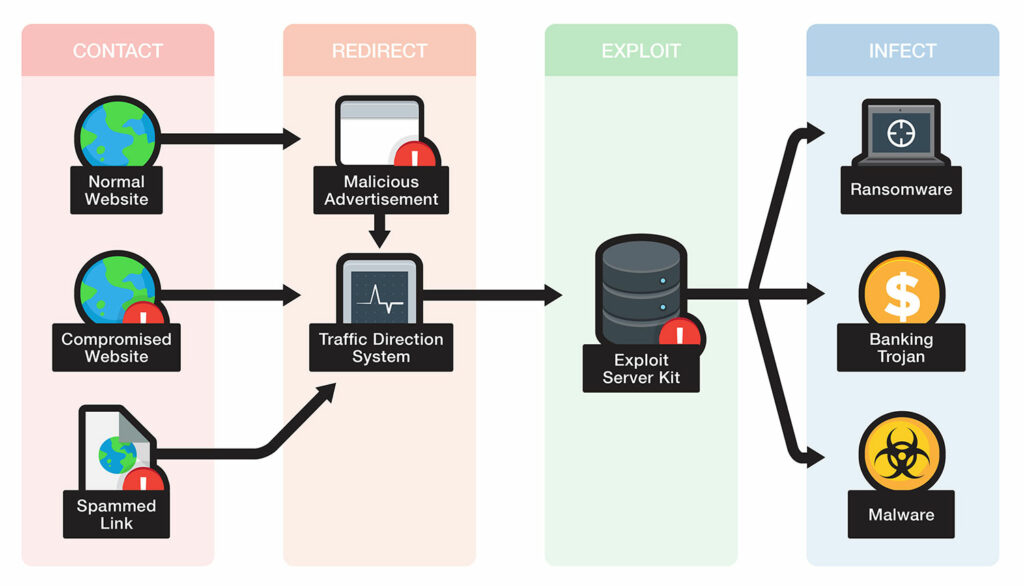
To perform its actions, a victim is responsible for the execution of this kind of malware delivery into the system. Below are the pointers that help in learning how it can infect devices.
- The user encounters a pop-up that claims to be an antivirus program but in reality, is fake. Moreover, it suggests you clean the malicious by running a program. But, in reality, it urges the users to download a trojan and welcome corruption onto their device. This can be termed as scareware.
- Attackers exploit a software vulnerability and thereupon install a Trojan through unauthorized access.
- A user invites a trojan by accessing an infected email attachment or tapping on a link to a corrupted website.
- Encountering a pop-up download in a harmful website.
- Downloading a program that is not published by a trustworthy site.
- The user is trying to connect a misleading Wi-Fi hotspot created by hackers to access their device.
- You are redirected to illegitimate sites having browser exploits that can bring the cybercriminals any file they want to download.
- If you are using any Trojan dropper then again it leads to several kinds of malware. Droppers and downloaders create a door of attacks through downloading, installing, and decompressing the core malicious modules. They are generally implemented as scripts or small applications.
Various Types of Trojan – List Of Different Viruses
Trojan can be categorized as per to the actions they can execute. Some of these types are included in the article below:
Exploit
Exploits take advantage of application software that uses data or code to run on your system.
Clampi Trojan
It can also be termed as Ligats and Ilomo. Clampi appears suddenly when the user performs activities like making financial transactions, accessing online banking, or entering credit card information. It is powerful enough to hide behind firewall and anti-malware software. It can reside in your system for long periods without your knowledge.
Backdoor
A backdoor Trojan enables malicious users to control the infected system. Such users can do anything on the computer. For instance, launching, sending, receiving, and displaying data, rebooting the computer, and deleting files. These trojans can create a bundle of malicious computers to form a zombie network for the only purpose of spreading criminality.
Banker Trojan
As its name suggests, a banker trojan is used to steal all your relevant information from your account. For example, banking systems, credit or debit cards, or e-payment systems.
Dropper Trojan
These applications prevent you to identify malicious programs. This way, they cover a place and infect the system.
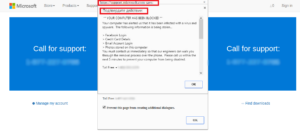
Cryxos Trojan
Cryxos Trojan emerges into the system with the call requests that generally fake in the disguised of scareware. You may also receive a text that states “Your device has been hacked” or “Your Computer is infected”. Not only this but it also shows you a contact number. When you dial the number, the malicious users pressurize you to provide some amount for assistance. While, in other cases, you can also be asked to provide remote access to your system. That can consequently trigger data theft and hijack.
Geost Trojan
You can remember Geost as an Android banking Trojan. It generally appears when the victims look for apps that are not available on Google Play. The application enables malware infection once it is downloaded properly. Also, you can only detect if the gang behind it made some security mistakes.
Qakbot Trojan
Qakbot Trojan is yet another advanced banking Trojan. Many people think of it as the first malware particularly designed for harvesting banking information.
Rootkit
Rootkits are used to hide certain infected objects or activities in the system. The main focus of the application is to extend the period a malicious program runs on the device.
Wacatac Trojan
Wacatac is one of the highly demanding Trojan threats. It can execute various malicious actions on the target system. Doing such activities phishing emails, software patches, and file sharing, over the infected network can corrupt your system. The user can bear a loss of data as it is quite confidential in sharing data with the hackers. Along with that, it gives remote access to them to conduct harmful tasks.
Remote Access Trojans
Abbreviated as RAT, Remote Access Trojans allow hackers to get full access to your system. Cybercriminals use these kinds of applications to spy on your online activities. Thereupon, they make money illegitimately. The software can distribute RATs to other corrupted devices if the user installs them in the system.
Mailfinder Trojan
Through these programs, the malicious users harvest email addresses from your computer. Later on, they send mass mailings of malware and spam to your contacts.
GameThief Trojan
Trojan Game Thief programs access user account information from online gamers.
Spy Trojan
As the name suggests, this malicious software can spy on what you are doing on your computer. For instance, it tracks all the info you enter via screenshot and keyboard. Also, it can access the list of all the applications running in your system.
Downloader Trojan
Some malicious users use Downloader Trojan to download and install new versions of malicious programs onto your computer.
You May Also Like: SECURE YOUR PERSONAL INFORMATION WITH NORTON SECURE VPN [UPDATED GUIDE]
IM Trojan
Trojan- IM programs can steal your logins and passwords. To do so, the malicious user uses instant messaging programs like Facebook, Messenger, Skype, WhatsApp, and so on. This kind of trojan enables the attacker to take over chat sessions, and send the Trojan to anyone from your contact list.
Ransom Trojan
Trojan- Ransom can modify data on the system so that it does not perform its functions properly. The cybercriminals only restore the computer’s data when you provide them the ransom they demand.
How to detect Trojan in your device
Now that we have understood the kinds of Trojan provide damages to the system. It’s time to know the several signs that will help you detect the presence of malicious software. So that, you can remove the virus as early as possible. Therefore, let’s learn below some of the most crucial signs that will make you aware of the virus.
- Frequents pop-ups that include not ads, browser, offering products, an antivirus scan. These can pave a way for kinds of malicious software with just a tap.
- If the device performances badly. For instance, running slowly with frequent crashes. Then, it might indicate that your device becomes corrupted with malware.
- The taskbar becomes extinct and changed altogether.
- During browsing, you will get back to unfamiliar websites.
- The task manager showing some unfamiliar programs even after you did not install them.
- You see some changes in the desktop like the screen resolution has altered or the color appears different.
- If spam emails having some uptick.
Well, you can remove some Trojans by disabling start-up items that don’t come from the trusted sources. To do so, you need to reboot the device into safe mode. Through this, the trojan becomes weak to prevent you from removing it.
You need to be aware of all the programs you are removing as Disabling the uncorrupted program can worsen the situation.
Can Trojan Infect Mobile Phones?
Yes, the Trojan virus can surely affect mobile devices, desktops, and laptop machines. It usually seems to be a legitimate application and program but hides different infectious sources within it. You can call it is just a fake variant of an app that stores malware. Pirate or Unofficial app markets are the leading sources of these kinds of unsuspecting users. You can consider the Clubhouse app as a fraudulent version of it. With these trojanized apps, hackers or cybercriminals can steal your data from your mobile phone. Consequently, make money by demanding ransom and sending text messages SMS of premium-rate.
Well, it is less concern topic for apple users as their mobiles contain Apple’s walled garden. That means you cannot access third-party apps from other platforms. But, can access only approved apps from your App Store. In short, the apps cannot make interference with other apps or have essential access to your phone’s operating system. Although, you might not get the same level of protection if your iPhone is jailbroken
Ways to Remove Trojan Virus
To get rid of these malicious activities, we must have acquired the best layer of good cybersecurity hygiene and antivirus protection. Well, you can either use the Norton Trojan removal tools or perform several functions given below:
DOs
- You need to protect your accounts with complex and unique passwords. Try to create a unique password for each of your accounts with a complex combination of letters, symbols, and numbers.
- Also, be more careful with email attachments. Before proceeding with any task, scan an email first. ‘
- Perform instant updates to the operating system software. whenever the company notifies you about it. Along with that, you need to examine updates for other software installed in your system.
- There should be proper security within your system. For that purpose, you need to install and run a security suite that is perfect for your safety. There should be frequent scans within the tool and Norton has removed this headache by providing automatic updates.
- Make sure to use a firewall to make the personal information and data safe and secure.
- Create a backup of your files regularly. It will aid you in restoring your data whenever a Trojan infects the system.
DON’Ts
- Don’t ever try to access a link in an email unless you know exactly what it is.
- Avoid downloading or installing programs if the publishes does not come from a trusted site.
- In addition, don’t click on the pop-up window that claims to provide you the prize money after finishing some tasks.
- Keep yourself away from unsafe websites by using Norton Trojan removal tools. These tools will notify you that you are making your way towards an unsafe site.
Final Note!
So, this is the guide about the Trojan virus. Once the trojan entered, it brings lots of issues and hindrances. So, try to keep all these do’s and don’t in mind for protecting yourself from future uncertainty. We wish that the guide proves successful to enlighten you with some known facts related to the virus. Yes, the virus can harm you both mentally and financially, but, through these do’s and don’ts, you block the opportunity for it to emerge. Also, if you want to have some advanced layer of protection then must consider the Norton Power Eraser. It has some dynamic features that can remove any virus from your system.
Author Profile
Latest entries
Technology2023.04.20How To Connect Roku To TV? Easy Guide To Follow
Technology2023.04.20How to Connect Nintendo Switch to TV? (With and Without Dock)
Technology2023.04.205 Best Barndominium Design Software (DIY & Professional)
Technology2023.04.20What Is The Relation Between Behavior-Driven Development And Agile Methodology?